This worrying outcome is made worse by the fact that criminals and fraud schemes are only becoming increasingly sophisticated. While not a new phenomenon, it’s the tempo of the increase that’s rather alarming and leading to what is now being referred to in the industry as “the great reset” expected to make waves in early 2023.
(Side note: This study by McKinsey on US banks considers how core banking platforms originating as far back as 1980 and 1990 – though still steady – lack agility, flexibility, and speed, initiating the conversation around resetting. Well worth the read.)
Back to the present day, and digital transformation continues to improve business operations. Unfortunately, with the addition of new features also comes the expansion of the attack surface. Real-time interception of sensitive communications, perfected phishing, account takeover fraud, sniffing to uncover unencrypted packets of information, and advanced malware are just some of the fraud risks and vectors that must be considered to prevent cyber criminals from breaching corporation networks and gaining access to inside-the-firewall systems. Because once successfully penetrated, the criminal can move around laterally from one system to the next without being detected, causing endless damage with immense restoration consequences.
As financial institutions embrace more contemporary ecosystems and the world adopts new approaches to digital banking, it’s clear that the traditional gated method of checking IDs at the door will no longer suffice. Fraud tactics have simply become too advanced. And there are also far more doors now than ever before.
Cue the reset realization, starting back at zero.
Zero trust
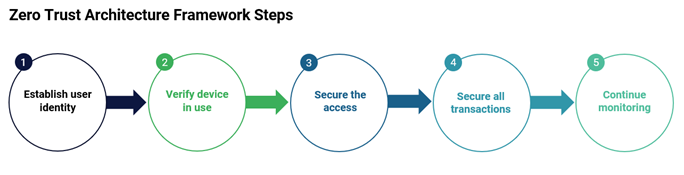
The term “zero trust” is often inadequately used as a buzzword and, in some instances, even to name new tech and security products. However, zero trust is actually a sophisticated architecture model and strategic framework appropriate for new-generation authentication systems and practices because of its diverse defense efforts that should be used in combination to address the ever-evolving attack trends. It’s also a great starting point for the shift in question.
Kaspersky defines zero trust as “never trust, always verify”, a holistic approach using open architecture and providing protection that is agile, responsive, adaptable, and sustainable. Zero trust unifies risk management by removing all trust within all transactions. When applied properly, it should still mitigate friction through a layered approach and combination of silent methods of authentication, where risk levels allow, to ensure protection fights fraud and not function.
The high-level flow starts by connecting users and applications, preventing a lateral movement of threats, reducing the attack surface, and embracing proxy-based architecture. This methodical protection navigates workforce, workload, and workplace, taking kindly to the shift from closed systems to ecosystems, and perimeter security to zero trust.
Context Aware™ Authentication
The key learnings for corporations are that identification alone is not enough. Introducing another layer is necessary. Linking identification with context (user, app, device, role, location, status, etc.) flags unexpected context behavior. We call it Context Aware™ Authentication.
When financial institutions enter this reset wave, the most important considerations for their customers will be to:
- Adopt a layered approach to authentication and customer identification with both active and passive authentication technologies,
- Consider the originating channel as well as cross-channel protection,
- Ensure the context of each interaction drives the use of the best available authentication mechanisms,
- Embrace multi-factor authentication (MFA),
- Continuously monitor transactions within themselves, and in real-time,
- Use contextual data from each interaction to inform and improve the next.
The benefits of zero-trust architecture
The benefits on offer make the framework appropriate for a variety of authentication use cases, including securing networks, protecting multi-cloud architecture/resources, safeguarding applications, complying with regulations, and requiring any user – internal or external – to be authenticated, authorized, and continuously validated.
Although a one-size-fits-all approach helped in ‘80s, companies should now customize tailored approaches that advance their security to safeguard both their customers and themselves.
Entersekt’s offering combines an ecosystem of third parties and both silent and active authenticators to create the most secure and seamless user experience. It considers the originating channel, transaction context, the use case, available authentication mechanisms as well as determining the most appropriate authentication journey, in real-time, and finally assessing risk signals in terms of the user’s usual behavior.
To learn more about how Entersekt can assist you with a zero-trust solution, get in touch with one of our experts.


