Usually, if something looks too good to be true, it probably is. This is especially true in our modern, digital world, where one wrong click can result in a customer having their identity or funds stolen by cybercriminals.
In this article, the third in our financial fraud deep dive series, we examine the dangers of social engineering attacks and how multi-factor authentication (MFA), and biometrics, provide strong, seamless security that protects your customers from malicious scams.
What is a social engineering attack?
A social engineering attack is a type of scam where a fraudster tricks their victim into revealing sensitive information, granting unauthorized access, or doing something that’s detrimental to them. Fraudsters make these attacks work by pretending to be a person or entity that the victim knows and trusts.
Here are some examples:
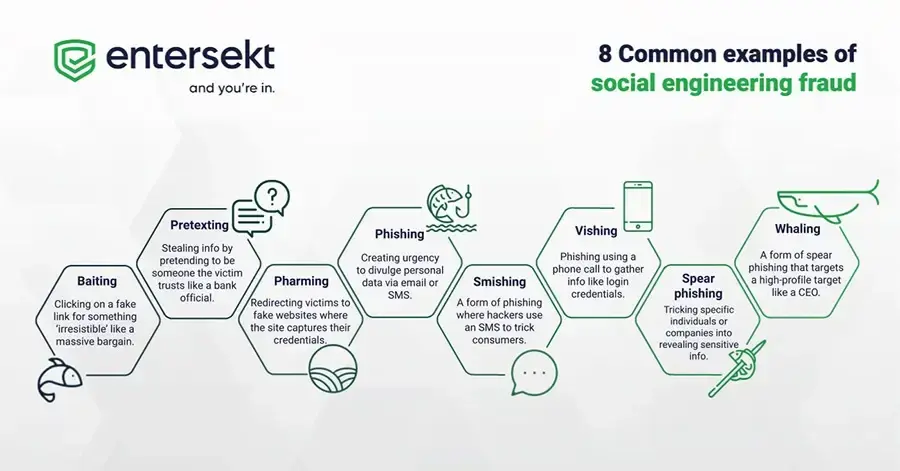
Cybercriminals use social engineering to obtain their victim’s personal data, like bank account details or a credit card number. Armed with this information, they can commit identity theft, open accounts in their victim’s name, or apply for loans, for instance.
What’s more, these attacks are often the entry point for a large-scale cyberattack on a bank or credit union’s entire network. The results can be devastating: From massive financial loss to identity theft, data breaches, or reputational damage to the financial institution (FI).
Typically, fraudsters follow these steps to commit social engineering fraud:
What’s more, these attacks are often the entry point for a large-scale cyberattack on a bank or credit union’s entire network. The results can be devastating: From massive financial loss to identity theft, data breaches, or reputational damage to the financial institution (FI).
Typically, fraudsters follow these steps to commit social engineering fraud:
- Conducting research about the victim or target business.
- Designing a suitable attack with the info they gather.
- Building trust with the victim by pretending to be someone they trust, such as a banking call center agent or IT support.
- Gaining access to the customer’s account and stealing their funds. Or gaining access to a network and kicking off a bigger attack scheme.
The success of these attack vectors hinges on psychological manipulation. And creating a sense of urgency that can cause customers, and bank employees, to make dangerous mistakes.
Why do social engineering attacks work?
Social engineering is all about human manipulation. These attacks focus on their victim’s sense of trust, greed, curiosity, or fear response to trick them into acting. Fraudsters manipulate these core emotions by, for instance, personalizing a phishing email with any data they’ve already attained on their victim.
Research indicates that adding personal info to phishing emails can increase the response rate from 16% to 72%!
Attackers either lure their victims into action by pretending to be from a government agency, such as the IRS, or pose as a well-known company, like UPS. Alternately, they trigger emotional responses, such as fear or greed, that often cause people to act without thinking clearly. For instance, a 90% discount on a new smart TV would be irresistible to many potential victims. Exploiting peoples’ curiosity and willingness to help are other ways fraudsters manipulate their targets.
The best rule of thumb when it comes to these scams is for customers to not automatically trust anything they receive via email or SMS, or anyone, merely because the communication or person seems real.
The best rule of thumb when it comes to these scams is for customers to not automatically trust anything they receive via email or SMS, or anyone, merely because the communication or person seems real.
Tip: Customers should be on the lookout for specific trigger words that fraudsters use in social engineering schemes, such as: limited, free, urgent, now or never, or last chance.
Education plays a vital role in preventing these attacks. Regular, up-to-date security training for all employees and banking customers can help them learn to spot red flags and respond quickly to anything suspicious.
Essentially, social engineering attacks are successful because they target humans — typically the weakest component in banking security. To strengthen your FI’s security, the right technology is a must, alongside continual fraud education.
How multi-factor authentication turns the tables
Because social engineering attacks are based primarily on stealing credentials, identity-proofing measures can help FIs recognize their customers and keep fraudsters out. These measures could include biometrics, ID verification, or multi-factor authentication (MFA) to block unauthorized access.
MFA adds an additional layer of protection against social engineering scams as it relies on more than one factor, such as passwords, to verify the customer’s identity. Modern solutions that combine authentication measures can protect your customers while giving them more choice of how they prove their identity.
Download our latest ebook: ‘Authentication reimagined’ to learn how innovative authentication technologies can keep your customers’ identities and transactions safe.
Seamless, secure customer verification with biometric authentication
Entersekt’s biometric authentication solution provides a simple way for organizations to integrate MFA into their digital banking channels.
Banking customers benefit from more secure, user-friendly login and payment experiences and the protection they need against social engineering and other modern fraud schemes, without adding unwanted friction.
In case you missed the second blog in this series, you can uncover three ways to win against account takeover fraud.


