The story behind digital authentication sounds familiar. Except, it didn’t start in a garage or basement, but in an MIT lab in 1961. There, a group of computer scientists got together and devised the concept of passwords. Little did they know the anguish it would cause over the next 60 years!
Unfortunately, passwords are not only inconvenient, but dangerous as well. It’s a problem the world has been grappling with for the last 20 years, at least. Luckily, the concept of trusted (or secure) endpoints is starting to gain traction and authentication is finally heading in the right direction – away from passwords.
Protecting banks with secure endpoints
When Entersekt was founded way back in 2009, we immediately recognized the value of secure endpoints and the problems they could solve. We made it our mission to assign these endpoints a few key attributes:
- We ensured that each endpoint instance was allocated a unique, once-off value.
- We made sure that each challenge-response mechanism was unique every time.
- We limited the “key” to a single use, unique to each mobile app, so that every “door” got a different “lock”.
- We seamlessly issued new keys to each new use case and made the linking easy.
- Quite importantly, we issued these keys to devices that users already had in their possession.
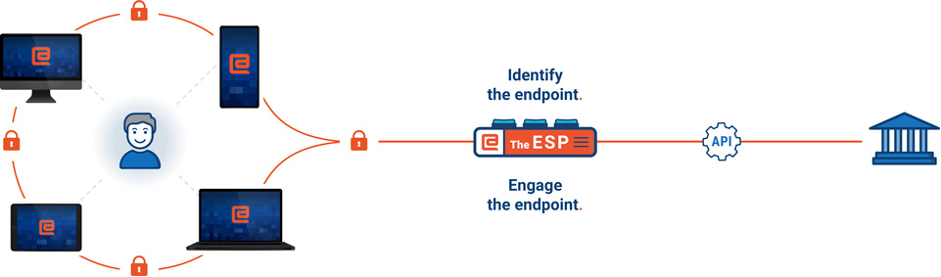
An ecosystem of secure endpoints
Applying these principles gave rise to a stable endpoint that could prove its legitimacy. And we’ve been protecting banks and their customers on this basis for many years. Yes, certain requirements have forced us to include passwords here and there, but the endpoint has always been the anchor.
Read why our VP Product, Simon Armstrong, agrees that passwordless authentication is the future.
Others who applied the same security principles arrived at similar solutions. The FIDO Alliance, launched eight years ago to tackle the world’s over-reliance on passwords, chose to focus mainly on protecting website logins. But their specifications overlapped with ours in several fundamental ways and, because the FIDO protocol delivered just a subset of our authentication product’s features, we were able to obtain certification for our product (Transakt) as a FIDO Ready U2F token.
A vision of endpoint perfection
When Android announced that FIDO would be built into their devices, things really started falling into place. Then Microsoft followed suit, adding it to their authentication setup in Windows (Windows Hello). Then, suddenly, with iOS 13.3, Safari started supporting external FIDO tokens. So, when Apple joined the FIDO Alliance many were already anticipating the unveiling that later took place at the WWDC.
Now, the endpoint puzzle is finally complete and later this year, all major desktop (Windows and macOS) and mobile (iOS and Android) operating systems will feature built-in FIDO authenticators operating as secure endpoints. Most of them will offer built-in multi-factor authentication as well, compliant with even European Strong Consumer Authentication (SCA) requirements!
Suffice to say, we are delighted that our vision of trusted endpoints has become a reality and that finally, context-specific identities can be provisioned into most consumer devices. Consumers can now trust in a physical device, not in some digital thing that can easily be lost or forgotten.
Of course, there are many challenges we still need to tackle. However, they pale in comparison to the potential that now exists to create exciting new customer journeys using a universal platform authenticator.
If this sounds like something you’d prefer over an outdated, 60-year-old password journey, speak to us.


