For decades, the financial services industry has relied on One-time PIN codes (OTPs) for both customer and payment authentication. But sophisticated shifts in computing power and mobile technology, along with an explosion of financial fraud, have rendered these single-use strings of digits obsolete, both in terms of security and convenience.
Financial institutions serious about conquering fraud, growing their revenue, and expanding their market share should, by now, be looking to the several secure customer authentication alternatives the industry has to offer. Here’s why.
Financial institutions serious about conquering fraud, growing their revenue, and expanding their market share should, by now, be looking to the several secure customer authentication alternatives the industry has to offer. Here’s why.
OTPs are no match for today’s fraud vectors
The intensity and sophistication of financial fraud attacks continue to rise inexorably. Security breaches at trusted companies regularly make the news, with stolen consumer data seemingly the currency of the digital underworld.
The resultant reputational damage and financial losses are at an all-time high, and yet organizations, including financial institutions around the world, continue to buy and deploy outdated, easily compromised authentication systems. In fact, in a 2022 Cyberthreat Defense Report, over 43% of decision-makers admitted to not having deployed even basic multi-factor authentication (MFA).
OTP, a passcode valid for a single login or online transaction and then discarded, is one such system that was originally developed to address the shortcomings of static passwords. And, while it solved an immediate need back then, the technology is no longer a match for today’s most common financial fraud vectors.
You see, all OTP systems still share the same inherent flaws:
The resultant reputational damage and financial losses are at an all-time high, and yet organizations, including financial institutions around the world, continue to buy and deploy outdated, easily compromised authentication systems. In fact, in a 2022 Cyberthreat Defense Report, over 43% of decision-makers admitted to not having deployed even basic multi-factor authentication (MFA).
OTP, a passcode valid for a single login or online transaction and then discarded, is one such system that was originally developed to address the shortcomings of static passwords. And, while it solved an immediate need back then, the technology is no longer a match for today’s most common financial fraud vectors.
You see, all OTP systems still share the same inherent flaws:
- Firstly, they are all “symmetric”, because the bank has access to the same secrets as its customer (the mobile carrier does too, in the case of SMS transmission).
- Secondly, OTP systems all remain reliant on browser-based communications back to the bank. This means that if a phishing site mimics the bank’s online banking or the browser is compromised, the customer’s credentials and the OTP can be harvested by fraudsters and immediately used to gain access to accounts and authenticate fraudulent transactions.
- And lastly, they’re clumsy and error-prone. While many mobile apps support auto-filling of OTPs sent via text message, or SMS, browser-based interactions still require users to switch applications, retrieve the code, and enter it correctly.
We’ll explore these problem areas in more detail below, showing why it’s time the financial services industry move on from this legacy technology.
SMS, the most popular (and vulnerable) channel
Because most people carry a mobile phone, it’s considered easy for banks to use text messages to deliver OTPs to their customers. As a means of customer authentication, it also eradicates the need for specialized hardware tokens, making it one of the most popular systems in use.
But – and we can’t emphasize this enough – SMS OTPs are not secure. Mobile phones are highly susceptible to Trojan attacks, which leverage open access to stored text messages specifically to intercept OTPs. The security of SMS also relies on the security of cellular networks, so the confidentiality of text messages cannot actually be assured by banks.
Mobile SIM swaps or SIM clones, number porting attacks, fake caller ID, and call forwarding scams operated by dishonest customer service representatives at mobile carriers all exploit insecure SMS networks and erode misplaced trust in the channel. In 2021 alone, $68 million was lost to SIM swap fraud in America!
But – and we can’t emphasize this enough – SMS OTPs are not secure. Mobile phones are highly susceptible to Trojan attacks, which leverage open access to stored text messages specifically to intercept OTPs. The security of SMS also relies on the security of cellular networks, so the confidentiality of text messages cannot actually be assured by banks.
Mobile SIM swaps or SIM clones, number porting attacks, fake caller ID, and call forwarding scams operated by dishonest customer service representatives at mobile carriers all exploit insecure SMS networks and erode misplaced trust in the channel. In 2021 alone, $68 million was lost to SIM swap fraud in America!

What’s more, SMS OTP is highly problematic in the context of regulatory frameworks, such as the Second Payment Services Directive (PSD2). While authentication via SMS OTP is still used by banks and tolerated by regulatory bodies to a degree, security experts have warned against them for years. Even as a second factor of authentication, SMS OTP falls short of making the Strong Customer Authentication (SCA) cut and is listed by the European Banking Authority as a method “to be avoided”.
The user experience challenge
OTP systems’ vulnerability to multiple forms of attack is a real concern for banks. Consumers, on the other hand, can be forgiven for focusing a great deal more on the extremely poor user experience OTPs offer.
Having to look up and enter unique codes during a login creates unwanted friction: it slows the user down, and the cumbersome re-entry process is subject to error. This is especially true for mobile users, since entering a long code on a mobile device is a challenge in any environment.
Having to look up and enter unique codes during a login creates unwanted friction: it slows the user down, and the cumbersome re-entry process is subject to error. This is especially true for mobile users, since entering a long code on a mobile device is a challenge in any environment.
Having to look up and enter unique codes during a login creates unwanted friction: it slows the user down, and the cumbersome re-entry process is subject to error.
With advances in technology, and the wide acceptance of methods such as biometric authentication, there’s also a growing expectation for absolute ease of use when operating online. Consumers see no reason why their bank cannot enable them to perform transactions on the go, or why they are expected to switch apps to enter an OTP when shopping online.
For financial institutions intent on providing a secure and convenient method for customers to transact online, there are luckily several new authentication solutions available today. These methods can eliminate virtually all types of fraud attacks – without causing unnecessary friction.
For financial institutions intent on providing a secure and convenient method for customers to transact online, there are luckily several new authentication solutions available today. These methods can eliminate virtually all types of fraud attacks – without causing unnecessary friction.
Context Aware™ Authentication solves risk and fraud concerns, without OTPs
Now more than ever, the financial services industry must balance the imperatives of powerful security, cost efficiency, and the demands of customers for convenience and a positive user experience if they’re to grow their customer base in this highly competitive market.
Context Aware™ Authentication achieves that balance with ease. It combines an ecosystem of third-party integrators and both silent and active authenticators to create the most secure and seamless user experience across all digital and payment channels.
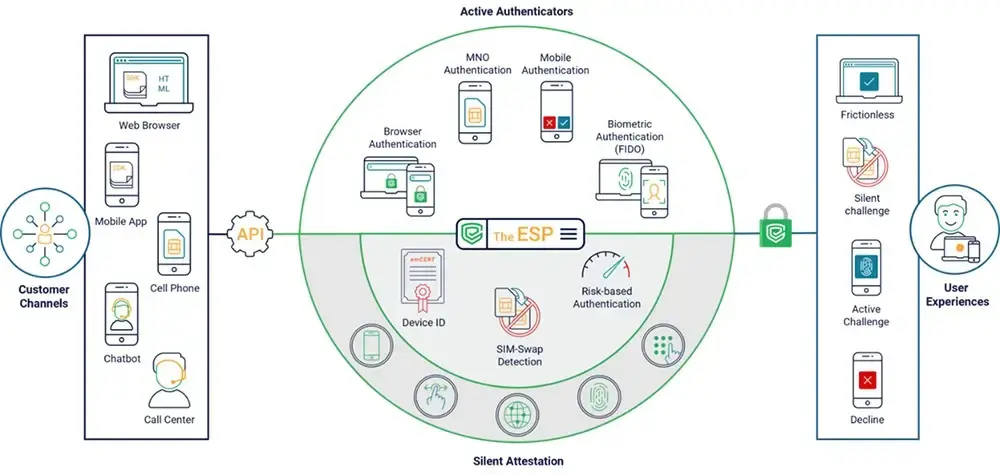
With Context Aware™ Authentication, FIs can:
- Secure all channels by providing a layered approach to customer authentication across multiple channels.
- Guard against all types of fraud by offering all-out, cross-channel protection rather than locking down a single channel in isolation.
- Deliver superior user experiences. Context Aware™ Authentication ensures the context of each interaction drives the use of the best available authentication mechanism, in real-time, thereby removing unnecessary friction.
Want to know more? Explore Context Aware™ Authentication from Entersekt, speak to an expert, or see our technology in action by booking a live demo.


